Step-by-Step Guide to Linux Security for Beginners: Your Comprehensive PDF Resource
Linux is known for its robust security features, making it a popular choice for individuals and organizations seeking a secure operating system. However, understanding and implementing Linux security measures can be intimidating, especially for beginners. To help new Linux users navigate the world of Linux security effectively, we present the “Step-by-Step Guide to Linux Security for Beginners” in PDF format.
This comprehensive resource offers a step-by-step approach, practical tips, and command-line references to enhance the security of your Linux systems. Let’s explore this guide and empower you to safeguard your Linux environment!
Understanding Linux Security:
The “Step-by-Step Guide to Linux Security for Beginners” provides a comprehensive introduction to Linux security. It explains the importance of securing your Linux systems and highlights common security risks and vulnerabilities. By understanding the fundamentals of Linux security, beginners can grasp the significance of implementing robust security measures.
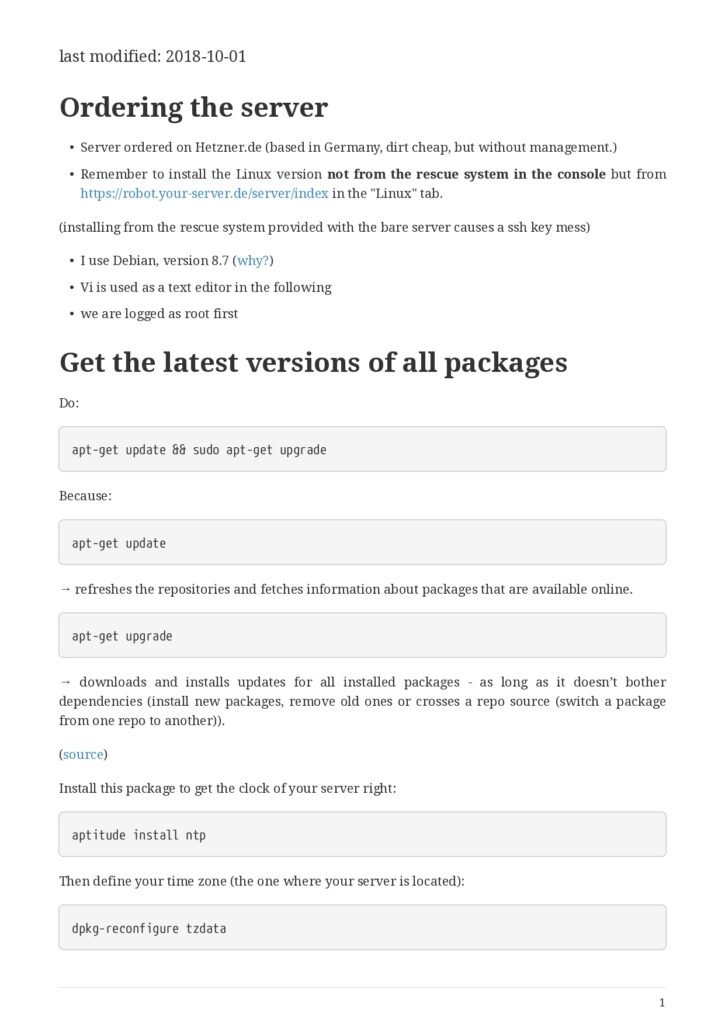
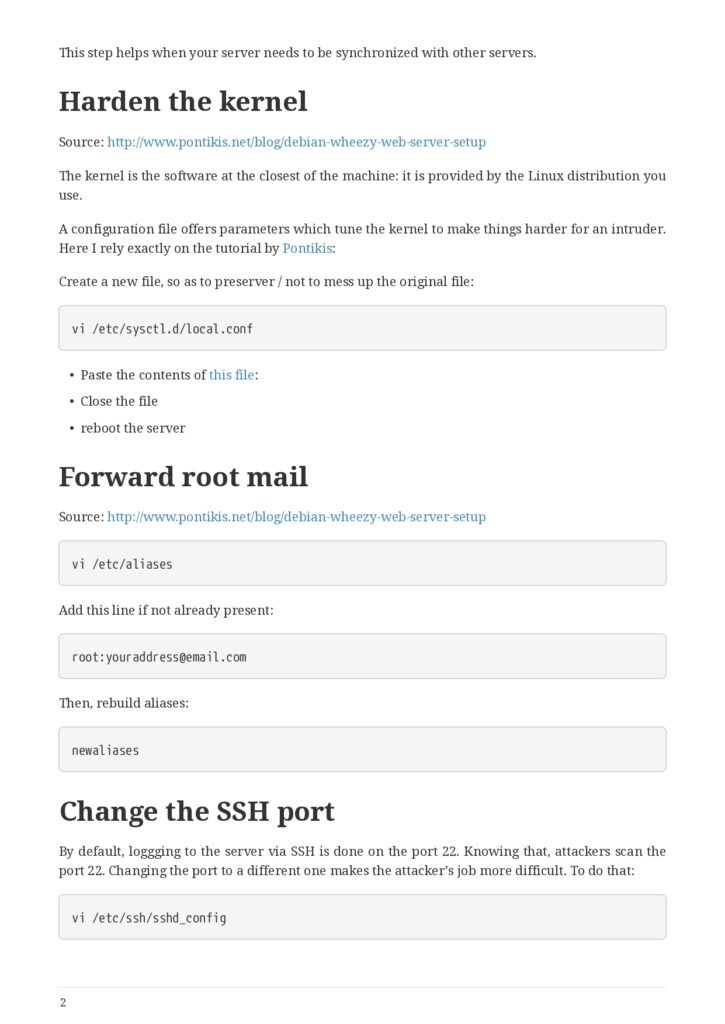
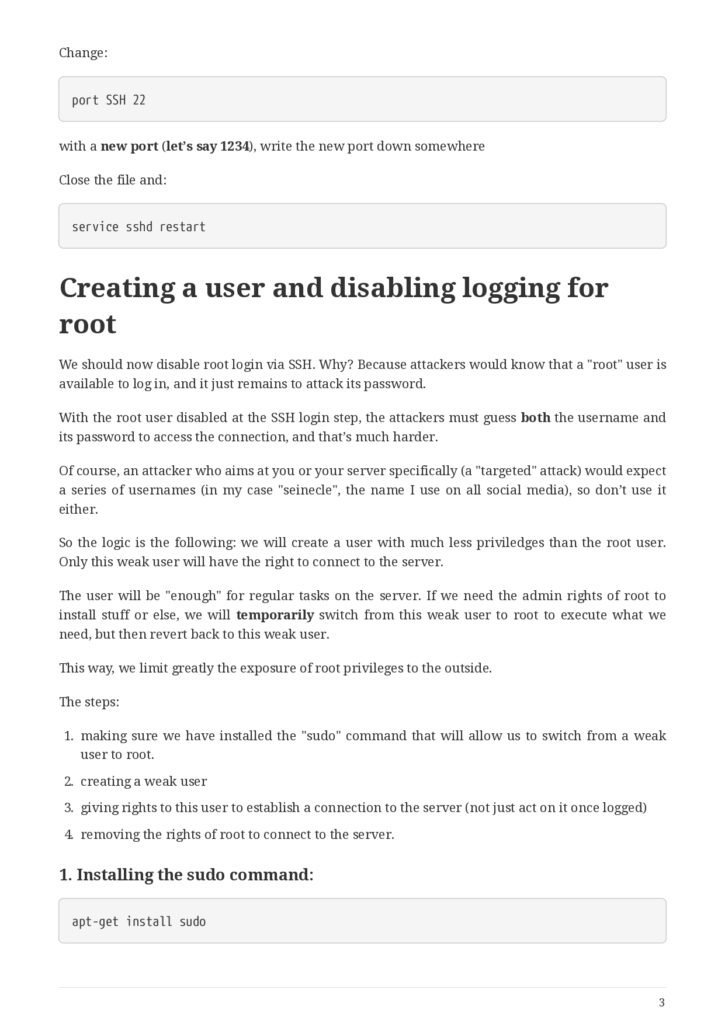
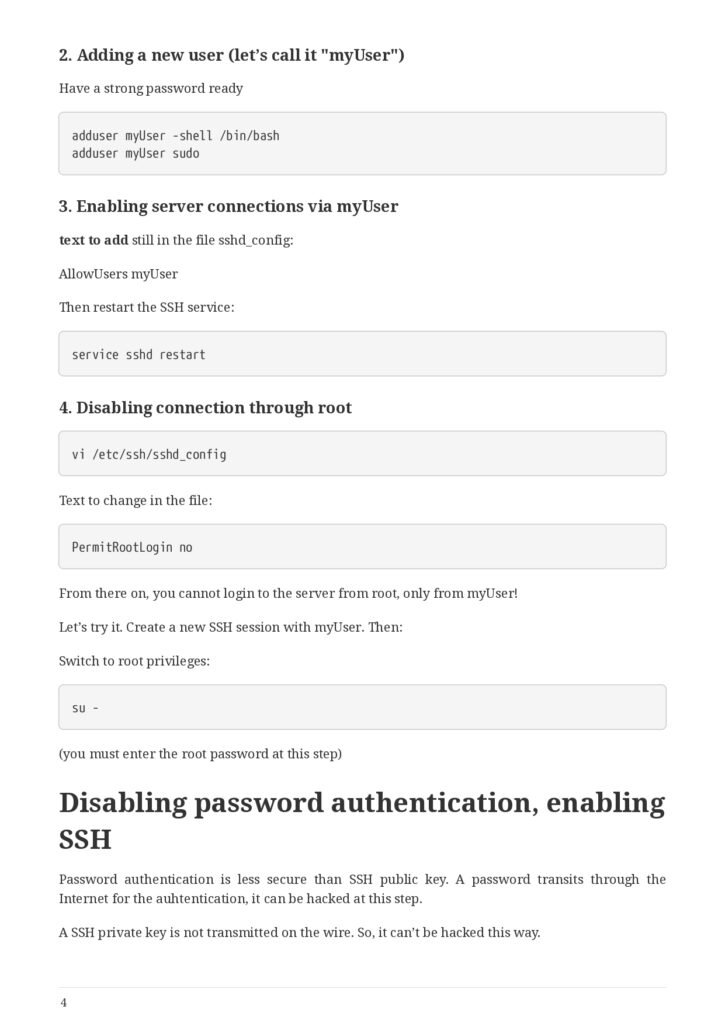
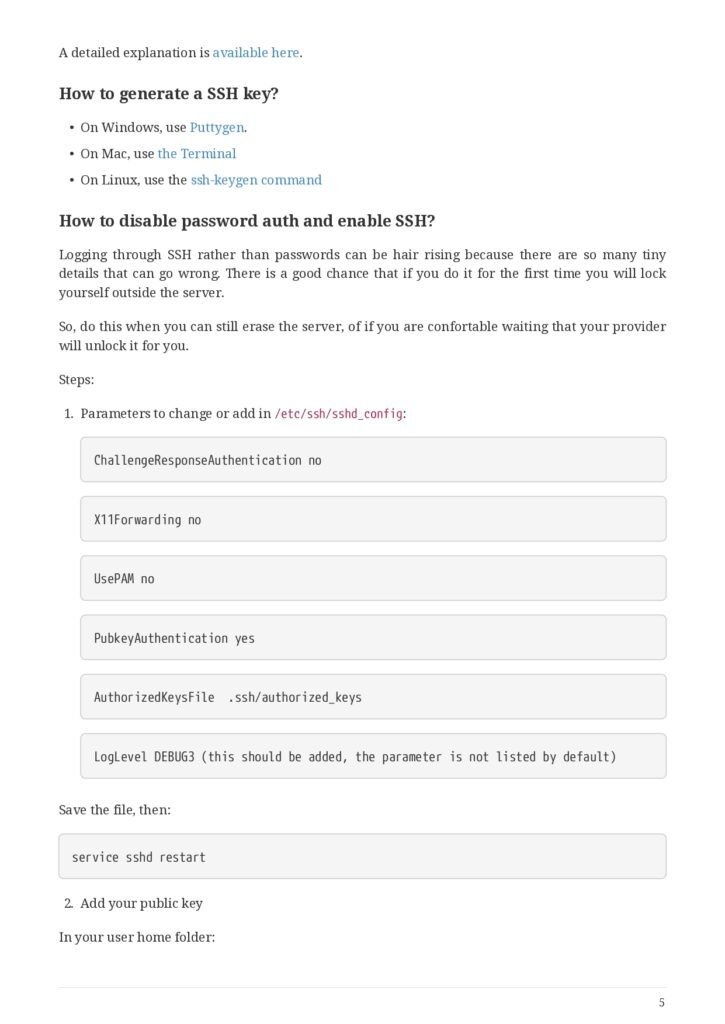
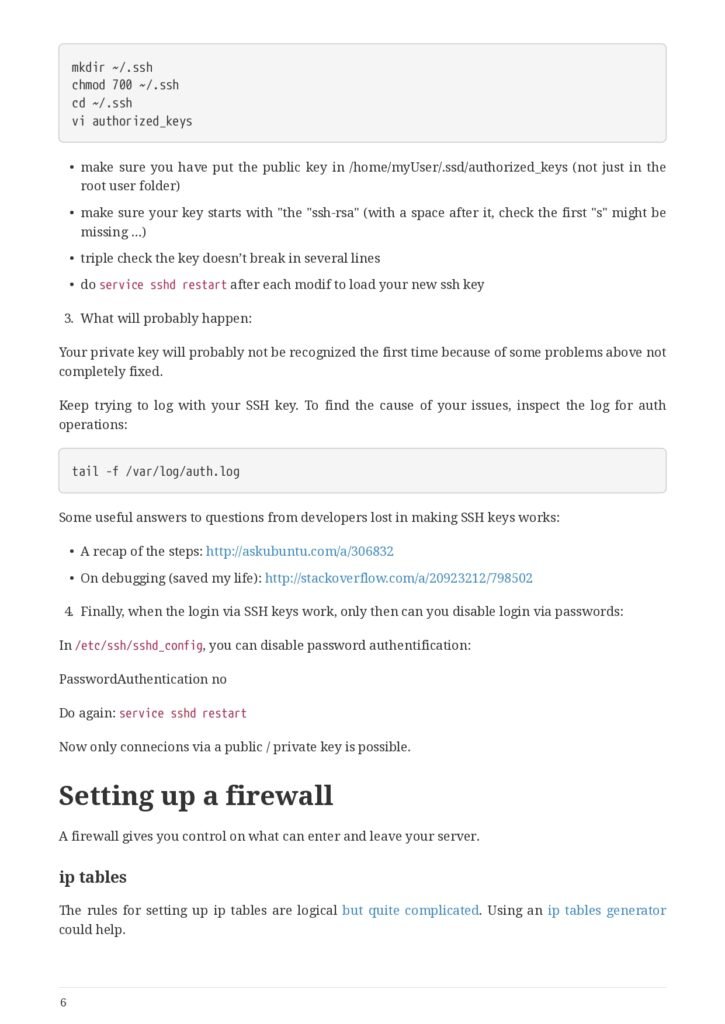
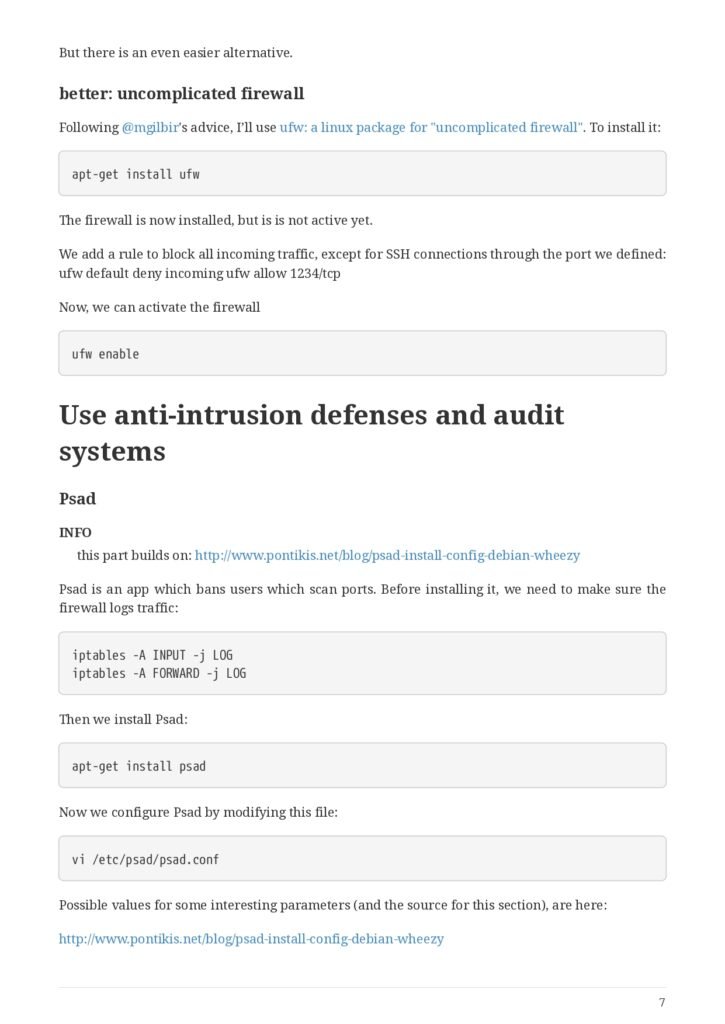
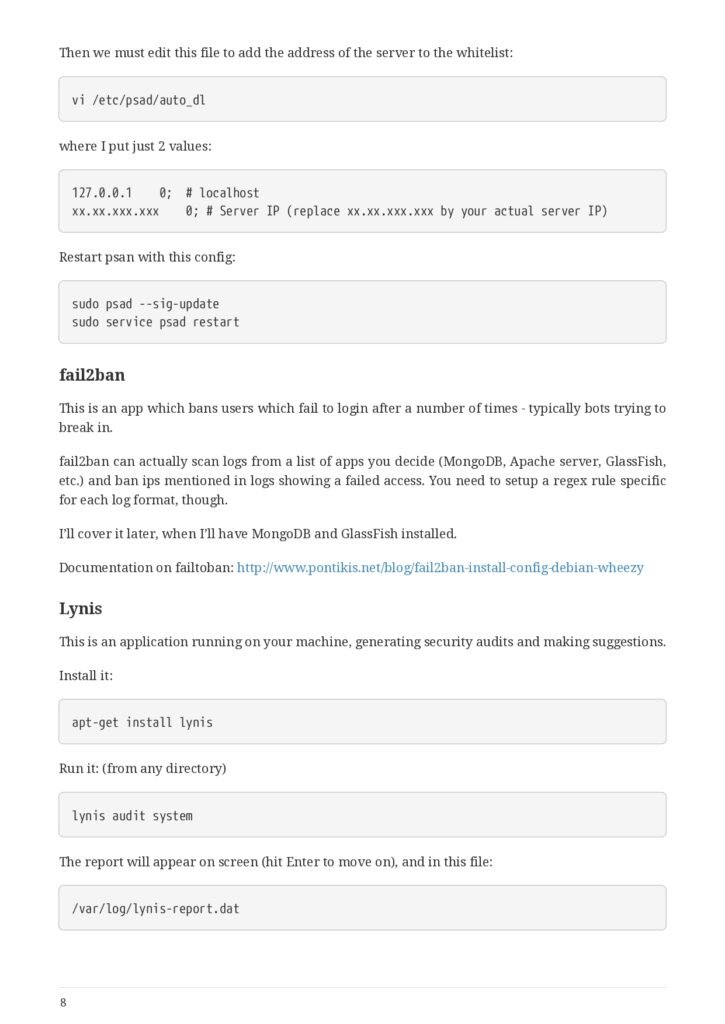
Table of Contents:
- Ordering the server
- Get the latest versions of all packages
- Harden the kernel
- Forward root mail
- Change the SSH port
- Creating a user and disabling logging for root
- Installing the sudo command:
- Adding a new user (let’s call it “myUser”)
- Enabling server connections via myUser
- Disabling connection through root
- Disabling password authentication, enabling SSH
- How to generate a SSH key?
- How to disable password auth and enable SSH?
- Setting up a firewall
- ip tables
- better: uncomplicated firewall
- Use anti-intrusion defenses and audit systems
- Psad
- failban
- Lynis
Step-by-Step Approach:
The “Step-by-Step Guide to Linux Security for Beginners” provides a structured and easy-to-follow approach. Each topic is presented in a step-by-step manner, guiding beginners through the process of implementing security measures. Practical examples and command-line references are provided to assist users in executing security tasks effectively.
Command-Line Reference:
The guide includes a command-line reference section, offering quick access to commonly used commands and their options related to Linux security. This reference material enables beginners to easily locate and utilize commands, simplifying the process of implementing security measures.
Conclusion:
The “Step-by-Step Guide to Linux Security for Beginners” in PDF format is a valuable resource for individuals new to Linux security. By offering a structured approach, practical tips, and command-line references, this guide empowers beginners to enhance the security of their Linux systems effectively.
Download the “Step-by-Step Guide to Linux Security for Beginners” PDF guide, keep it readily accessible, and embark on your journey to secure your Linux environment. Whether you’re an individual Linux user or an organization with Linux systems, this guide will assist you in implementing sound security practices.
By leveraging the step-by-step approach, practical tips, and command-line references within the guide, you can confidently enhance the security posture of your Linux systems. Empower yourself with the knowledge and skills to protect your data and maintain the integrity of your Linux environment.
Download the “Step-by-Step Guide to Linux Security for Beginners” PDF guide and embark on your journey to strengthen the security of your Linux systems. Secure your Linux environment and embrace the power of Linux with confidence!
Nu Of Pages:
11 Pages
To Download PDF:
Explore Our Linux Notes From here


